Long Context RAG Performance of LLMs
databricks
AUGUST 12, 2024
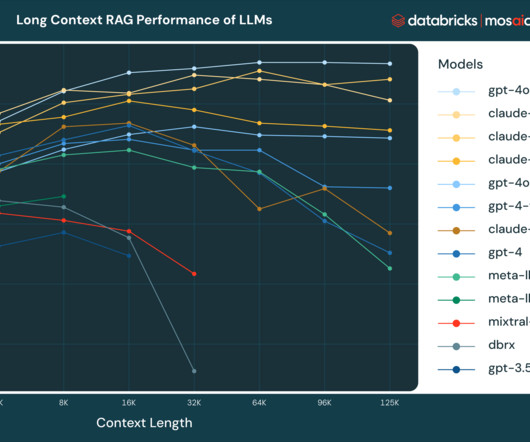
Retrieval Augmented Generation (RAG) is the most widely adopted generative AI use case among our customers. RAG enhances the accuracy of LLMs by.
databricks
AUGUST 12, 2024
Retrieval Augmented Generation (RAG) is the most widely adopted generative AI use case among our customers. RAG enhances the accuracy of LLMs by.

Cisco Wireless
AUGUST 12, 2024
This blog explores the paradigm shift brought about by AIOps, which combines the power of AI and automation to streamline IT operations, enhance decision-making, and drive proactive problem resolution.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Dataversity
AUGUST 12, 2024
One of the most important questions about using AI responsibly has very little to do with data, models, or anything technical. It has to do with the power of a captivating story about magical thinking. There’s a set of beliefs driven by over-exuberant AI hype – that AI is going to revolutionize everything! How can […] The post Ask a Data Ethicist: How Can We Set Realistic Expectations About AI?

databricks
AUGUST 12, 2024
The blog explores data streams from NASA satellites using Apache Kafka and Databricks. It demonstrates ingestion and transformation with Delta Live Tables in SQL and AI/BI-powered analysis of supernova events.
Cisco Wireless
AUGUST 12, 2024
Learn how Cisco Foundation partners Raspberry Pi Foundation and Digital Opportunity Trust are supporting and nurturing the creativity, resiliency, and leadership of youths worldwide through sustainability programs and digital resiliency.

InfoQ Articles
AUGUST 12, 2024
Incidents are often perceived as extraordinary aberrations, unconnected to "normal" work. For over twenty years, the field of Resilience Engineering has aimed at flipping this approach around — by understanding what makes incidents so rare (relative to when and how they do not happen) and so minor (relative to how much worse they can be) and deliberately enhancing what makes that possible.

VIAVI Solutions
AUGUST 12, 2024
We now know that observability goes well beyond traditional network monitoring practices to take real-time visibility to the next level. It is worth taking a closer look at the ingredients needed to convert disparate data sources into actionable insights. With the quest for observability sometimes curtailed by network complexity, a holistic approach is essential. holistic: […] The post Connecting the Dots of Observability appeared first on VIAVI Perspectives.
IT Networking Pro Today brings together the best content for advertising professionals from the widest variety of industry thought leaders.

CATO Networks
AUGUST 12, 2024
Introduction At RSA Conference 2024, Cato Networks introduced Cato CTRL (Cyber Threats Research Lab), which is our cyber threat intelligence (CTI) team. Cato CTRL protects organizations by collecting, analyzing and reporting on external and internal threats, utilizing the data lake underlying the Cato SASE Cloud Platform. For 2024, Cato CTRL is publishing quarterly threat reports that provide an overview of the threat landscape.

Dataversity
AUGUST 12, 2024
We live in a data-driven culture, which means that as a business leader, you probably have more data than you know what to do with. To gain control over your data, it is essential to implement a data governance strategy that considers the business needs of every level, from basement to boardroom. A proper data […] The post 4 Ways Embedded BI Improves Data Governance appeared first on DATAVERSITY.

Packet Pushers
AUGUST 12, 2024
Take a Network Break! This week we cover a judge’s ruling that Google is monopolist and potential outcomes, the HPE/Juniper acquisition clearing regulatory hurdles, and Microsoft flipping the bird at Delta’s legal threats. HPE Aruba Networking adds NDR for IoT devices, Fortinet fortifies its DLP capabilities via acquisition, Azure lets you stack logs in different.
Let's personalize your content