12 Days of Learning to Hustle in the New Year
Cisco Wireless
DECEMBER 16, 2024
Join us for 12 days of skill-building that could transform your 2025.

Cisco Wireless
DECEMBER 16, 2024
Join us for 12 days of skill-building that could transform your 2025.
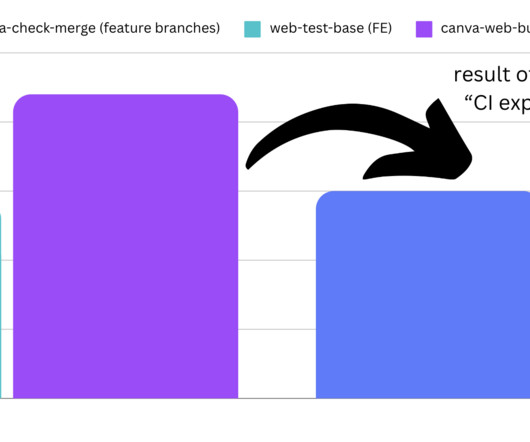
Canva Dev
DECEMBER 16, 2024
How we improved our continuous integration build times from hours to less than 30 minutes.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Cisco Wireless
DECEMBER 16, 2024
Every year, I take time to think deeply about which technology trends will truly shape the year to come. As we stand on the cusp of 2025, the technology landscape is marked by economic and geopolitical uncertainty, tectonic shifts in consumer behavior, an expanding digital ecosystem, and intense pressure for businesses to adopt and integrate AI into their core operations.

Clear to Send
DECEMBER 16, 2024
[link] Meet our guest, Tiago Rodrigues, the CEO of the Wireless Broadband Alliance (WBA). Hes here to introduce us to the WBA, what the organization does, and how they shape the wireless industry. Weve had Tiago on the show in previous episodes and in this new interview, he provides us with an update on how OpenRoaming has been doing. Tiago highlighted some real-world use cases where OpenRoaming was highly successful.

Cisco Wireless
DECEMBER 16, 2024
U.S. government regulation has an impact on PQC availability, with different certified encryption methods being required for products handling government info.

Obkio
DECEMBER 16, 2024
Learn how to effectively monitor firewall performance, identify common issues, troubleshoot, and choose the right toolset.

Cisco Wireless
DECEMBER 16, 2024
We sat down with Mike (Mac) McNamara, Vice President and Head of Network Engineering for Boost Mobile, to discuss the companys ambitious 5G network deploymentand Ciscos pivotal role.
IT Networking Pro Today brings together the best content for advertising professionals from the widest variety of industry thought leaders.

Cisco Wireless
DECEMBER 16, 2024
Celebrate a season of gratitude and growth with Ciscos 360 Partner Program. Built on collaboration, it offers partners flexibility and support to thrive, setting new standards for success in the new year.

Cloudera Blog
DECEMBER 16, 2024
In the last year, weve seen the explosion of AI in the enterprise, leaving organizations to consider the infrastructure and processes for AI to successfullyand securelydeploy across an organization. As we head into 2025, its clear that next year will be just as exciting as past years. Here, Cloudera experts share their insights on what to expect in data and AI for the enterprise in 2025.

Packet Pushers
DECEMBER 16, 2024
Take a Network Break! This is our final show for 2024. We start with critical vulnerabilities in Ivanti and OpenWrt, and then discuss what effect a proposed bill from US Senator Ron Wyden would have on telecom security (short answer: more paperwork but unlikely to improve protection). Extreme Networks announces a new AI platform that. Read more » Take a Network Break!

databricks
DECEMBER 16, 2024
While nearly 80% of the worlds data is in video format, enabling search and understanding on video data has historically been a challenging.

Roger Perkin
DECEMBER 16, 2024
How to remove all Docker Containers? To remove all Docker containers from your server run the command Note: The “-f” option will force the removal of a running container How to run docker compose without terminal output in terminal?
Confluent
DECEMBER 16, 2024
Announcing Confluents JavaScript Client for Apache Kafka (CJSK), an officially maintained and easy-to-use client based on librdkafka, and kept up to date with Apache Kafka features.

Dataversity
DECEMBER 16, 2024
In todays digital age, managing and minimizing data collection is essential for maintaining business security. Prioritizing data privacy helps organizations ensure they only gather necessary information, reducing the risk of data breaches and misuse. This approach addresses potential vulnerabilities at their source, mitigating the impact of breaches and avoiding regulatory penalties as scrutiny over privacy […] The post Focusing on Data Privacy: Building Trust and Strengthening Security ap

NW Kings
DECEMBER 16, 2024
The transport layer is a crucial component of the OSI model , serving as the fourth layer in the network architecture. The protocols of transport layer play a significant role in data transmission across the network, ensuring reliable communication between sender and receiver. This blog will explore the key protocols within the transport layer, focusing on TCP ( Transmission Control Protocol ) and UDP (User Datagram Protocol) in detail.

Dataversity
DECEMBER 16, 2024
Predictions are funny things. They often seem like a bold gamble, almost like trying to peer into the future with the confidence we inherently lack as humans. Technologys rapid advancement surprises even the most seasoned experts, especially when it progresses exponentially, as it often does. As physicist Albert A. Bartlett famously said, The greatest shortcoming […] The post AI Predictions for 2025: Embracing the Future of Human and Machine Collaboration appeared first on DATAVERSITY.

Network Lessons
DECEMBER 16, 2024
The post QoS LLQ Queue Starvation appeared first on NetworkLessons.com.

CATO Networks
DECEMBER 16, 2024
Executive Summary Modern ransomware attacks have evolved beyond simple encryption to deploy sophisticated double extortion tactics. Threat actors now systematically exfiltrate sensitive data before encrypting systems, ensuring leverage even when victims have robust data backups. Some ransomware gangs have even abandoned encryption altogether, recognizing that the threat of data exposure often proves more compelling for ransom payment.

Cockroach Labs
DECEMBER 16, 2024
Its a tale of two approaches to turn PostgreSQL into a distributed SQL database solution: forking PostgreSQL or rewriting the SQL layer in a compatible way. This has resulted in a common talking point: If a vendor forks PostgreSQL are they inherently more PostgreSQL compatible?

CloudFaire
DECEMBER 16, 2024
Cloudflare Radar celebrated its fourth birthday in September 2024. As weve expanded Radars scope over the last four years, the value that it provides as a resource for the global Internet has grown over time, and with Radar data and graphs often appearing in publications and social media around the world, we knew that we needed to make it available in languages beyond English.
Let's personalize your content