The Sidecar Pattern Explained: Decoupling Operational Features
ByteByteGo
DECEMBER 19, 2024
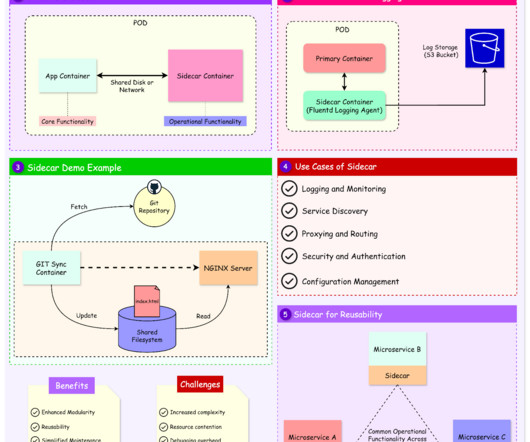
Design patterns are reusable solutions to common problems in software design. They provide a structured approach to solving architectural challenges without reinventing the wheel each time. The sidecar pattern is one such design pattern that has gained prominence in modern software engineering. At its core, the sidecar pattern pairs a secondary process or service (the "sidecar") with a primary application to handle complementary tasks.























Let's personalize your content