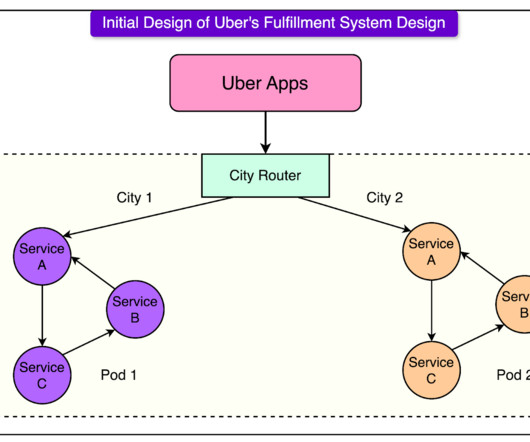
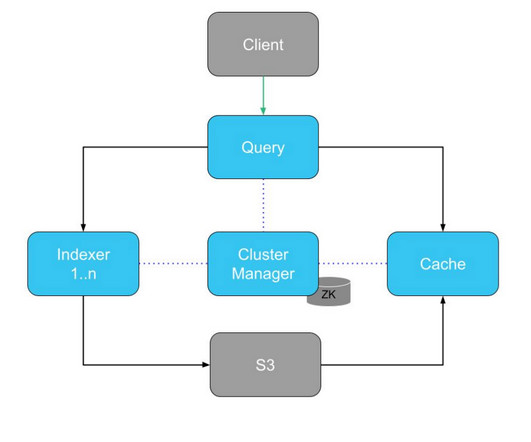
Uber’s Billion Trips Migration Setup with Zero Downtime
ByteByteGo
NOVEMBER 19, 2024
📅Meet your EOY deadlines – faster releases, zero quality compromises (Sponsored) If slow QA processes and flaky tests are a bottleneck for your engineering team, you need QA Wolf. Their AI-native platform , backed by full-time QA engineers, enables their team to create tests 5x faster than anyone else. New tests are created in minutes and existing tests are updated almost instantaneously. ✔️Unlimited parallel test runs ✔️15-min QA cycles ✔️





















Let's personalize your content