Resilience and Redundancy in Networking
Kentik
MAY 8, 2023
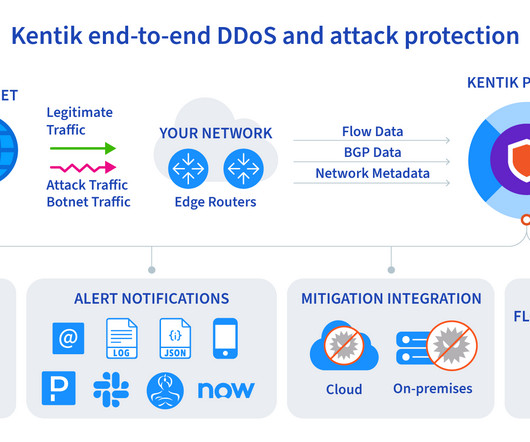
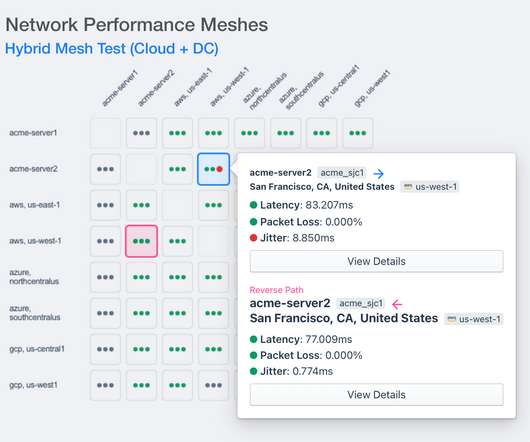
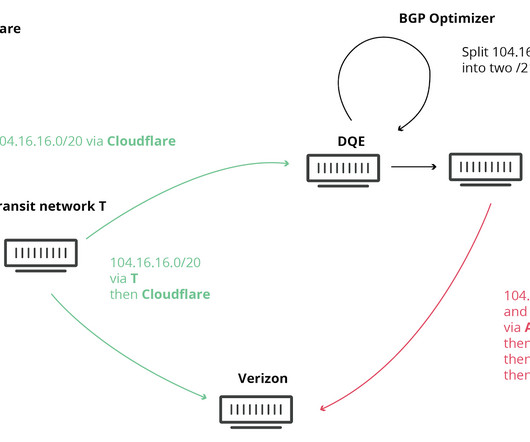
This includes the ability to: Dynamically adjust to changes in network topology Detect and respond to outages Route around faults in order to maintain connectivity and service levels. While redundancy is a significant contributor to network resilience, other mechanisms, protocols, and methods can also contribute to overall network resilience.










Let's personalize your content