DNS Zone Setup Best Practices on Azure
Cloudera Blog
FEBRUARY 12, 2024
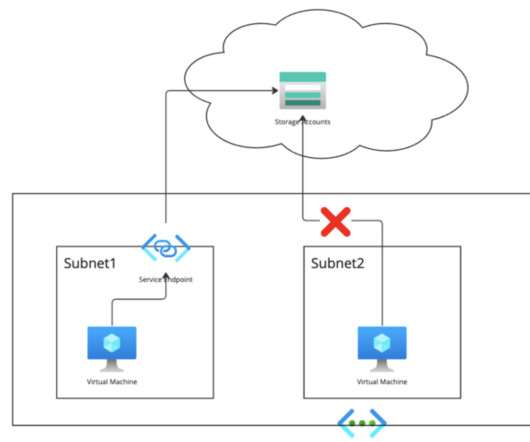
In Cloudera deployments on public cloud, one of the key configuration elements is the DNS. If the DNS is set up less ideal than it could be, connectivity and performance issues may arise. In this blog, we’ll take you through our tried and tested best practices for setting up your DNS for use with Cloudera on Azure.











Let's personalize your content