EP143: DNS Record Types You Should Know
ByteByteGo
DECEMBER 21, 2024
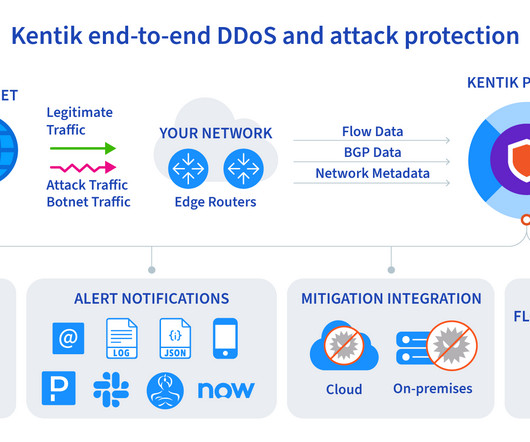
This week’s system design refresher: 8 Most Important System Design Concepts You Should Know (Youtube Video) DNS Record Types You Should Know Polling Vs Webhooks API Vs SDK! Here are the 8 most commonly used DNS Record Types. They are used for websites and services that support the IPv6 protocol.






























Let's personalize your content