CCNA: TCP SEQ and Port Number
The Network DNA
JUNE 19, 2024
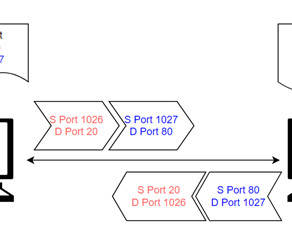
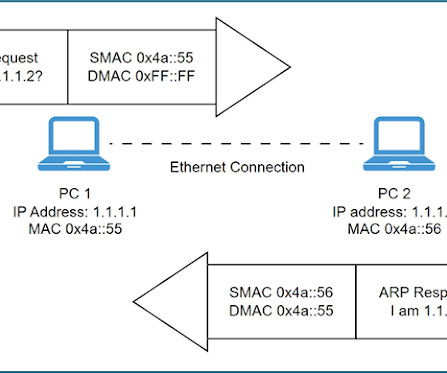
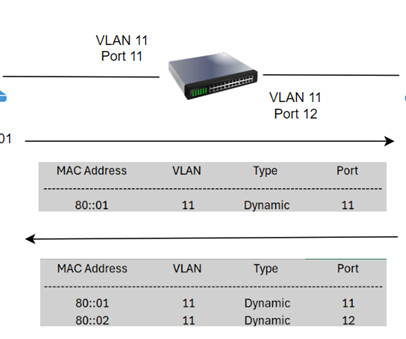
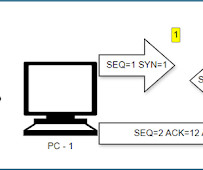
CCNA: TCP Sequence & Port Number This article can be read as the second part of the previous article CCNA: 3-Way Handshake where we discussed what makes TCP a reliable protocol for transmitting information. Lets discuss the TCP SEQ and Port numbers in this article. These applications are identified using the port numbers.










Let's personalize your content