The malware threat landscape: NodeStealer, DuckTail, and more
Engineering at Meta
MAY 3, 2023
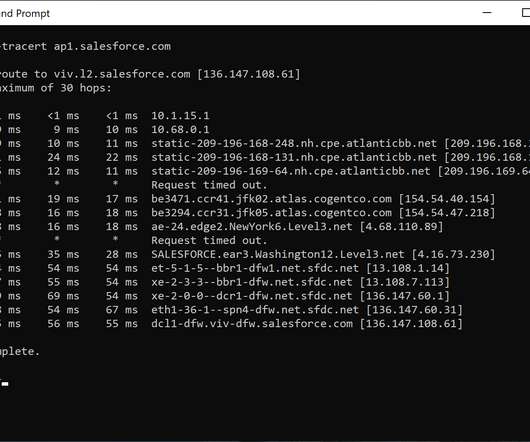
Novel NodeStealer malware: An in-depth analysis In late January 2023, our security team identified a new malware NodeStealer that targeted internet browsers on Windows with a goal of stealing cookies and saved usernames and passwords to ultimately compromise Facebook, Gmail, and Outlook accounts. environment.











Let's personalize your content