EP147: The Ultimate API Learning Roadmap
ByteByteGo
JANUARY 25, 2025
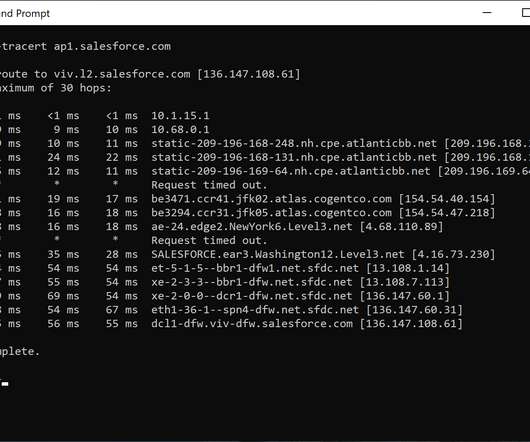
Explained With Simple Terms Session, Cookie, JWT, Token, SSO, and OAuth 2.0 API Terminologies Various API terminologies, such as HTTP versions, cookies, and caching, need to be understood. After DNS resolution, the requests reach the app servers. Session, Cookie, JWT, Token, SSO, and OAuth 2.0 Code First v.s.










Let's personalize your content