Rethinking Enterprise VPN Solutions: Designing Scalable VPN Connectivity
CATO Networks
NOVEMBER 2, 2020
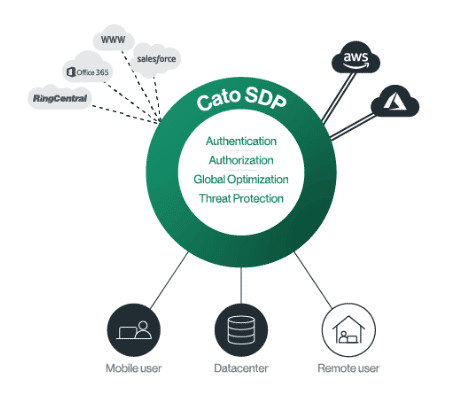
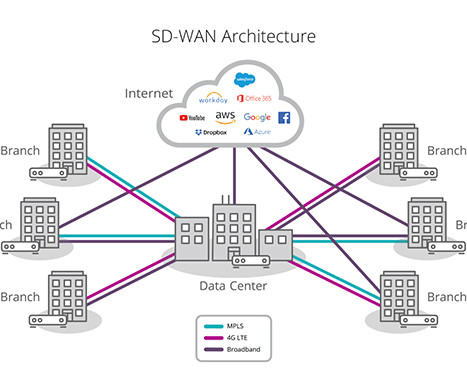
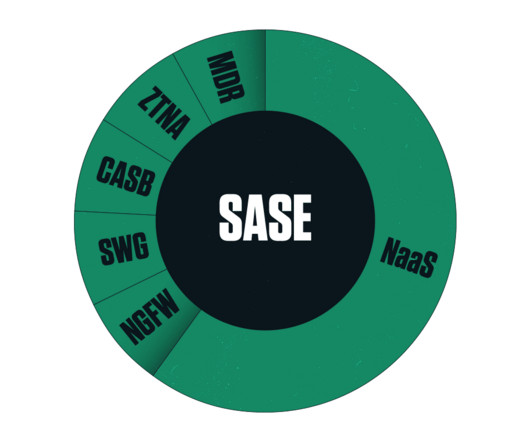
To keep business functioning as best as possible, enterprises need to provide secure remote connectivity to the corporate network and cloud-based resources for their remote workers. In the early days of Coronavirus lockdowns, some countries saw a surge in VPN use that more than doubled the typical pre-pandemic demand.





































Let's personalize your content