Concerns Grow As AFRINIC’s Funds Are Frozen Over IPv4 Dispute
Kentik
AUGUST 5, 2021
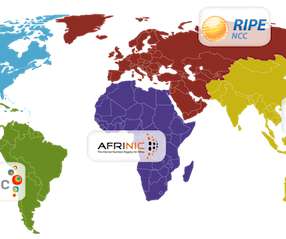
An evolving legal dispute involving AFRINIC, Africa’s regional internet registry, has led to the freezing of the organization’s bank account and concerns about the stability of the continent’s internet operations. As the available supply of IPv4 addresses became exhausted and IPv6 adoption lagged, the demand for IPv4 naturally increased.














Let's personalize your content