Concerns Grow As AFRINIC’s Funds Are Frozen Over IPv4 Dispute
Kentik
AUGUST 5, 2021
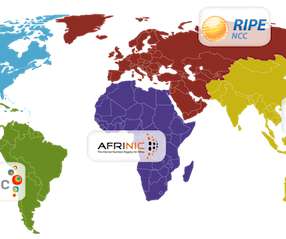
An evolving legal dispute involving AFRINIC, Africa’s regional internet registry, has led to the freezing of the organization’s bank account and concerns about the stability of the continent’s internet operations. It was also Ron’s analysis that contributed to LACNIC’s decision to revoke DDoS-Guard’s address space. How did we get here?













Let's personalize your content