Which SSE Can Replace the Physical Datacenter Firewalls?
CATO Networks
APRIL 6, 2023
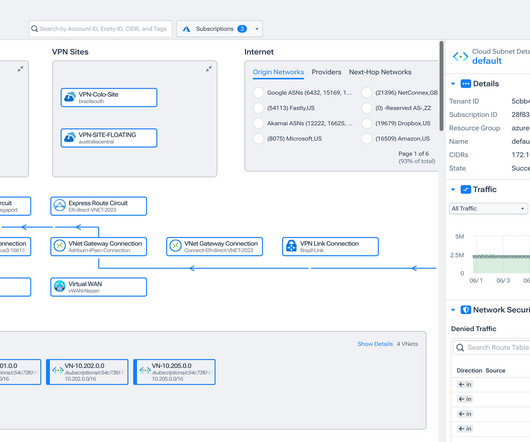
But only a few can securely cloudify the datacenter firewall. This is because datacenter firewalls dont just address the need for secure Internet access, which is the main SSE capability. In this blog post, we explore which capabilities a datacenter firewall-replacing SSE needs to have. Download the White Paper 3.


























Let's personalize your content