Watch Meta’s engineers discuss optimizing large-scale networks
Engineering at Meta
JANUARY 27, 2023
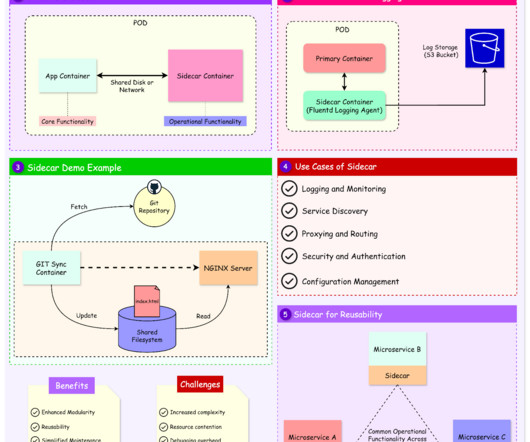
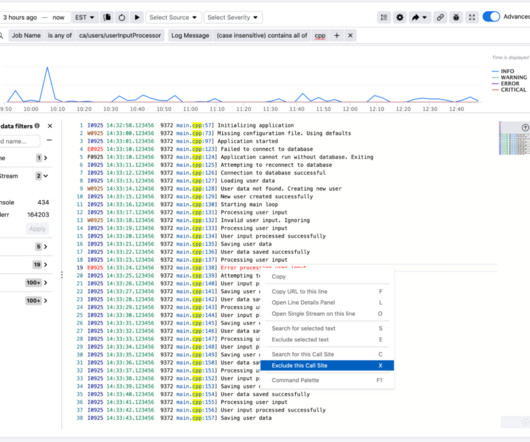
Operational Efficiency and Metrics Improvements: Traditional network metrics such as packet loss and jitter are too specific to the network/host and do not provide correlation between the application behavior and network performance.






































Let's personalize your content