Best Examples of IoT Applications and IoT Devices: (Internet of Things)
NW Kings
DECEMBER 10, 2024
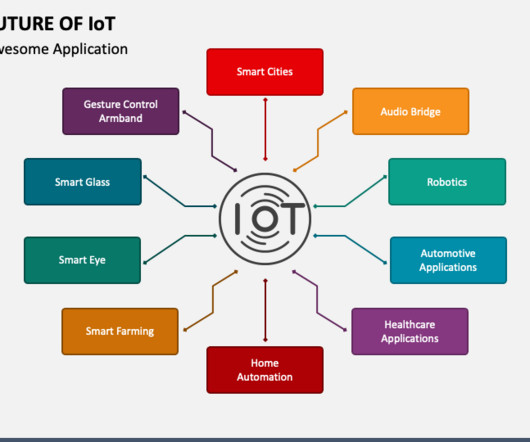
This blog will explore numerous examples of IoT applications, showcasing how these connected devices transform everyday life and industries. Smart Home Devices Smart homes are a prime example of IoT applications. For example, a smart thermostat can reduce energy consumption while youre away, saving money on utility bills.














Let's personalize your content