NPM, encryption, and the challenges ahead: Part 1 of 2
Kentik
OCTOBER 12, 2021
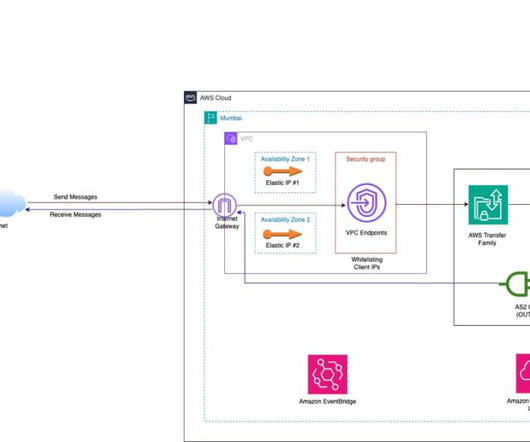
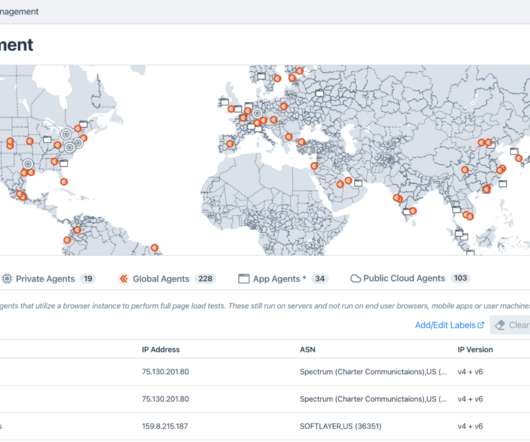
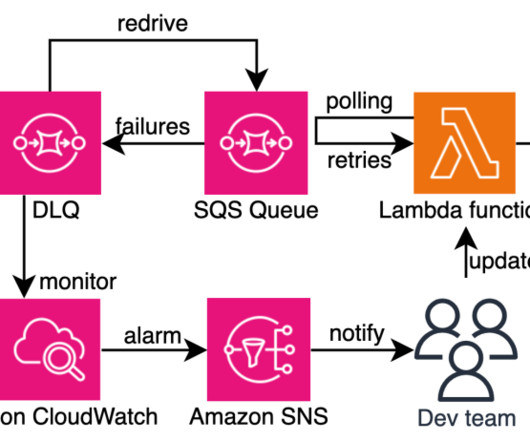
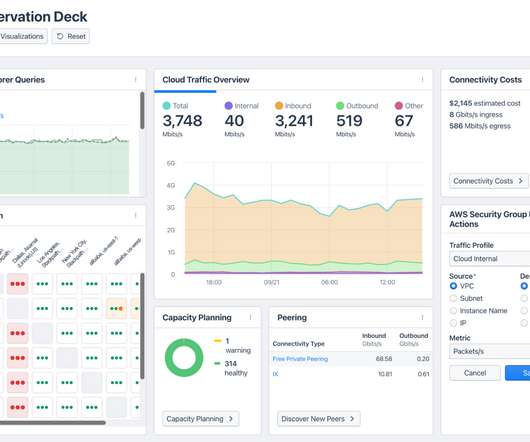
It’s interesting to observe how encryption and network performance monitoring (NPM) have evolved over time. When I first entered the networking industry right out of college, many applications sent passwords over the network in clear text, unencrypted. Encrypted passwords came along as did token authentication.





































Let's personalize your content