Building end-to-end security for Messenger
Engineering at Meta
DECEMBER 6, 2023
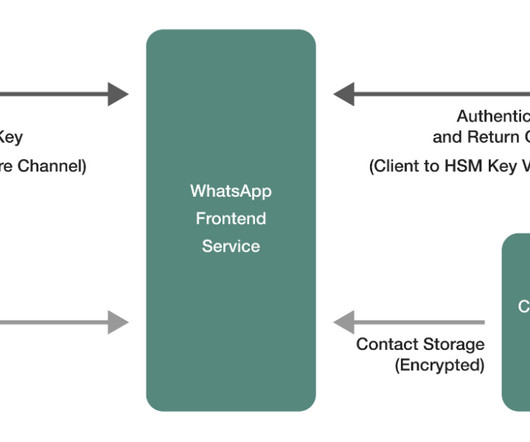
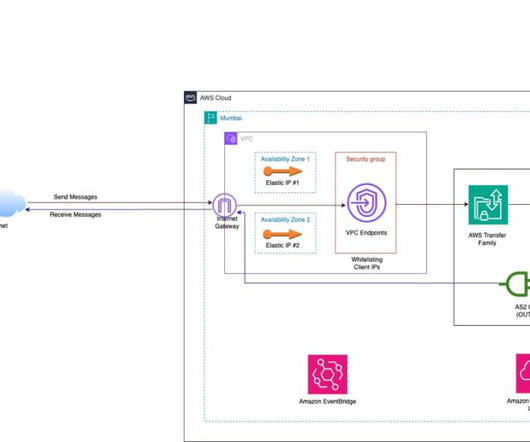
We are beginning to upgrade people’s personal conversations on Messenger to use end-to-end encryption (E2EE) by default Meta is publishing two technical white papers on end-to-end encryption: Our Messenger end-to-end encryption whitepaper describes the core cryptographic protocol for transmitting messages between clients.









































Let's personalize your content