How CyberArk is streamlining serverless governance by codifying architectural blueprints
AWS Architecture
OCTOBER 11, 2024
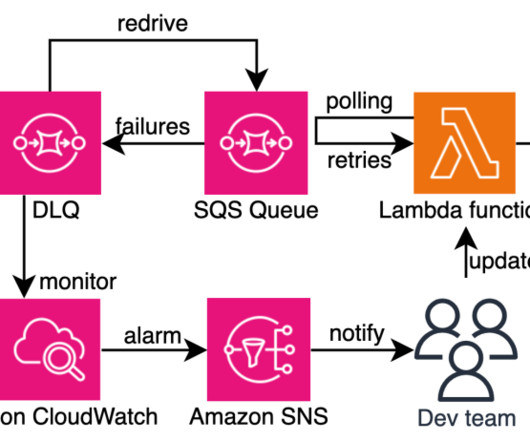
Organizations embracing serverless architectures build robust, distributed cloud applications. As organizations grow and the number of development teams increases, maintaining architectural consistency, standardization, and governance across projects becomes crucial.
































Let's personalize your content