Article: Application Level Encryption for Software Architects
InfoQ Articles
DECEMBER 18, 2020
Challenges of building application-level encryption for software architects. By Eugene Pilyankevich.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

InfoQ Articles
DECEMBER 18, 2020
Challenges of building application-level encryption for software architects. By Eugene Pilyankevich.

InfoQ Articles
OCTOBER 5, 2021
CEW Systems' Bi-Symmetric Hybrid Encryption System provides a new approach to post-quantum encryption that has been designed to be immune to a variety of attacks, including brute force attacks, man-in-the-middle attacks and rolljam attacks.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Kentik
OCTOBER 12, 2021
It’s interesting to observe how encryption and network performance monitoring (NPM) have evolved over time. When I first entered the networking industry right out of college, many applications sent passwords over the network in clear text, unencrypted. Encrypted passwords came along as did token authentication. What is NPM?

PubNub
JANUARY 8, 2025
Which data in your application are sensitive? Encryption in Android Using PubNub Kotlin SDK

Kentik
JANUARY 24, 2022
Natively, it can’t tell us with a high degree of certainty the actual application behind the flow. Natively, it can’t tell us with a high degree of certainty the actual application behind the flow. NetFlow v5), let’s explore different methods that have been used to determine the application behind a flow. Don’t rely on ports.

CATO Networks
NOVEMBER 19, 2024
Introduction In todays digital environment, encrypted traffic has become the norm, with over 90% of web communications now utilizing encryption. While this secures data in transit, it has become a blind spot for enterprises, enabling attackers to hide malware within encrypted channels.

PubNub
JANUARY 8, 2025
Building secure, encrypted web chat applications just got easier. Learn from our step-by-step guide.

Engineering at Meta
DECEMBER 6, 2023
We are beginning to upgrade people’s personal conversations on Messenger to use end-to-end encryption (E2EE) by default Meta is publishing two technical white papers on end-to-end encryption: Our Messenger end-to-end encryption whitepaper describes the core cryptographic protocol for transmitting messages between clients.

Engineering at Meta
APRIL 13, 2023
Key transparency solutions help strengthen the guarantee that end-to-end encryption provides to private, personal messaging applications in a transparent manner available to all. It is among the most widely used deployments of end-to-end encryption and relies on public key cryptography first developed in the 1970s.

InfoQ Articles
NOVEMBER 16, 2022
However, they are more difficult to manage than the application layer, since Kubernetes is designed for stateless applications. Apache ShardingSphere is the ecosystem to transform any database into a distributed database system and enhance it with sharding, elastic scaling, encryption features, and more. By Trista Pan.
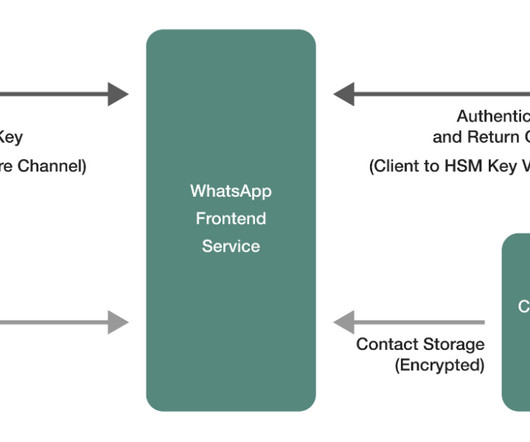
Engineering at Meta
OCTOBER 22, 2024
As part of WhatsApp’s new feature to privately add and manage your contacts on WhatsApp across linked devices, we’re announcing a novel encrypted storage system we’ve designed called Identity Proof Linked Storage (IPLS). IPLS is a novel system at WhatsApp that allows users to store their contact names in an encrypted way.

CloudFaire
DECEMBER 20, 2024
Now, applications built using Cloudflare Calls and OpenAIs Realtime API can now support multiple users across the globe simultaneously seeing and interacting with a voice or video AI. There are similar opportunities if your application is built for consumers: broadcasts and global livestreams can become much more interactive.

Cloudera Blog
OCTOBER 8, 2024
Enterprise developers began exploring proof of concepts (POCs) for generative AI applications, leveraging API services and open models such as Llama 2 and Mistral. Businesses are now allocating dedicated budgets and building infrastructure to support AI applications in real-world environments.
CATO Networks
SEPTEMBER 22, 2022
A growing percentage of Internet traffic is protected by encryption. According to Google , approximately 95% of web browsing uses the encrypted HTTPS protocol. This trend toward traffic encryption has been driven by a few different factors. The move toward data encryption is a mixed blessing for cybersecurity.

Engineering at Meta
MARCH 6, 2024
We’re sharing how we enabled third-party interoperability (interop) while maintaining end-to-end encryption (E2EE) and other privacy guarantees in our services as far as possible. WhatsApp and Messenger both use the tried and tested Signal protocol as a foundational piece for their encryption.

ByteByteGo
JANUARY 25, 2025
Youtube video) The Ultimate API Learning Roadmap 30 Useful AI Apps That Can Help You in 2025 10 Essential Components of a Production Web Application How do we design effective and safe APIs? Here’s a roadmap that covers the most important topics: Introduction to APIs API is a set of protocols and tools for building applications.
Kentik
OCTOBER 20, 2021
In part 1 of this series, I talked a bit about how encryption is shaping network performance monitoring (NPM). Unless the complaint is coming from all remote users of an application, individuals suffering from slowness are on their own to figure out how to optimize connection speeds. Let’s dive in deeper now…. API testing.

InfoQ Articles
OCTOBER 28, 2024
Securing cell-based architecture is essential to fully capitalize on its benefits while minimizing risks. To achieve this, comprehensive security measures must be put in place. Organizations can start by isolating and containing cells using sandbox environments and strict access control mechanisms like role-based and attribute-based access control.

CATO Networks
OCTOBER 18, 2020
Identities of entities can be associated with people, groups of people (branch offices), devices, applications, services, IoT systems or edge computing locations. In short, SASE is meant to be one holistic platform for the complete network, covering all edges, all traffic, and all applications, i.e., the entities in the definition above.

InfoQ Articles
NOVEMBER 9, 2022
Obfuscation is often mistaken with encryption, but they are different concepts. In this article, we introduce the topic of code obfuscation, with emphasis on string obfuscation. Obfuscation is an important practice to protect source code by making it unintelligible. By Michael Haephrati, Ruth Haephrati.
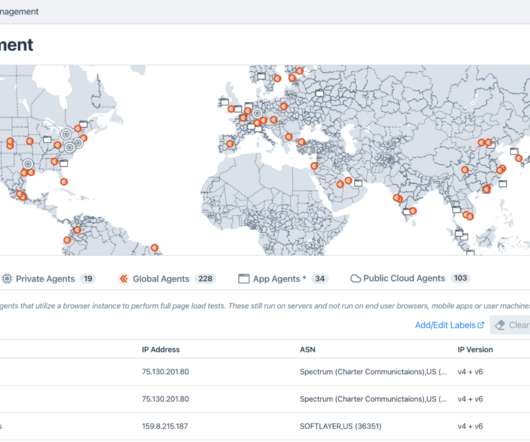
CATO Networks
DECEMBER 14, 2021
The new Cato Management Application that we announced today certainly brings a scalable, powerful interface. We enhanced security reporting with an all-new threats dashboard and opened up application performance with another new dashboard. Behind the Cato Management Application is a completely rearchitected backend.

CloudFaire
DECEMBER 27, 2024
Todays roundup blog post shares two exciting updates across our platform: our cross-platform 1.1.1.1 & WARP applications (consumer) and device agents (Zero Trust) now use MASQUE , a cutting-edge HTTP/3 -based protocol, to secure your Internet connection. Additionally, DEX is now available for general availability.

Juniper
JANUARY 10, 2025
However, the bad news is that this new era also brings the ability to break current VPN encryption algorithms. One fundamental issue is that we wont truly know how quantum-resistant these algorithms are until widespread application of quantum computing. Hybrid PQC is one such approach.
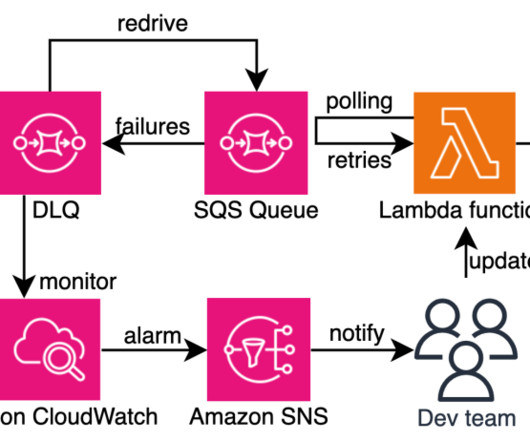
AWS Architecture
OCTOBER 11, 2024
Organizations embracing serverless architectures build robust, distributed cloud applications. Application developers should focus on delivering business value efficiently, rather than navigating the complexities of building and operating distributed architectures while adhering to organizational best practices.

Engineering at Meta
MAY 22, 2024
In the future, significant advances in quantum computing will make it possible for adversaries to decrypt stored data that was encrypted using today’s cryptosystems. How Meta is approaching the migration to PQC Meta’s applications are used by billions of people every day. Existing algorithms have reliably secured data for a long time.

CATO Networks
NOVEMBER 19, 2024
Shadow AI lurks in the background for organizations Shadow AI refers to the unauthorized or unsanctioned use of AI applications and tools within an organization without the knowledge or approval of IT departments or security teams. However, TLS inspection can break applications and access to some domains.

Cloudera Blog
JANUARY 7, 2025
However, a few foundational components are needed to make this possible: Unified Runtime : Run applications and manage data seamlessly across environments without extensive rewrites. Data Encryption: Organizations encrypt data both in transit and at rest to prevent unauthorized access.

CATO Networks
OCTOBER 10, 2024
In cybersecurity, Zero Trust Network Access ( ZTNA ) has emerged as a pivotal solution, ensuring secure access to applications regardless of user location. Benefits of ZTNA ZTNA enhances enterprise security by ensuring only authenticated and authorized users can access specific applications. What is ZTNA?

CATO Networks
AUGUST 29, 2018
Few enterprises can risk sacrificing application performance and worker productivity in exchange for lowering their telecom costs. We run an encrypted software-defined overlay across all the backbone segments of our cloud infrastructure. There are too few good routes available. Which Tradeoff to Choose? But whats the alternative?

Confluent
SEPTEMBER 20, 2019
This blog post goes over: The complexities that users will run into when self-managing Apache Kafka on the cloud and how users can benefit from building event streaming applications with a fully managed service for Apache Kafka. Key characteristics of a fully managed service that you can trust for production and mission-critical applications.

Cloudera Blog
JUNE 6, 2024
The Role of AI in Banking 2024 continues to witness the rapid development of AI and its applications, with GenAI leading the charge. Gartner’s predictions also estimate 80% of enterprises will adopt GenAI APIs and models or deploy GenAI-enabled applications in production environments by 2028. trillion to US$4.4

CATO Networks
MAY 12, 2022
TLS is designed to increase security by encrypting data end-to-end between two points, ideally preventing bad actors from having visibility into the traffic of your web session. However, threat actors have also come to see the value in utilizing TLS encryption for delivering malware and evading security controls.

Kentik
DECEMBER 15, 2021
Special application solutions we offer include: CDN - We provide load-balanced application delivery and backup solutions that leverage nationwide networks provided by large ISPs, IDC centers, distributed by region.

AWS Architecture
NOVEMBER 18, 2024
In this post, we highlight must-see sessions for those building resilient applications and architectures on AWS. Cloud resilience refers to the ability for an application to resist or recover from disruptions, including those related to infrastructure, dependent services, misconfigurations, transient network issues, and load spikes.

CATO Networks
APRIL 18, 2022
Immediate Loss of Productivity Organizations depend almost entirely on data and applications for their daily operations, including making payments, creating products and delivering and shipping them. One of the ways attackers gain these amounts is encrypting organizational data, and requiring a payment for instructions on how to decrypt it.

Confluent
JULY 31, 2019
If you’re like most users, chances are that Confluent Platform is rapidly becoming the new standard for integrating your data and applications to uncover new insights about your business, build real-time customer experiences, and create new business models. Automate Kafka operations for production environments.

CATO Networks
JULY 20, 2021
Sidewalks new encryption method Doing encryption right is not an easy task, especially when introducing new methods. While Amazon promises its triple encryption will make data transfer safe, their new methodology has not been battle tested yet. This is not behavior enterprises would expect from their devices.
Akins IT
NOVEMBER 22, 2017
Office 365 Built-In Applications Microsoft has built several of its applications into Team so all tools are accessible on the spot. Teams was built off the basis of Office 365 Groups cross-application that allows users to share and preserve information across different applications.
Kentik
MARCH 19, 2020
In many infrastructures, the inflection points are at the network edge, where VPN gateways authenticate and encrypt remote-access traffic. More advanced VPNs can do this by application type. NetOps teams today are contending with a surge in traffic coming from remote employees, and businesses are relying on them to ensure productivity.
CATO Networks
MAY 18, 2023
CISAs Zero Trust Maturity Model helps enterprises measure this journey based on five pillars: Identity, Devices, Networks, Applications and Data. Pillar 3: Network/Environment To achieve the zero trust principles of Network Segmentation, Threat Protection and Encryption, a new, dynamic architecture is required.
CATO Networks
JUNE 4, 2024
Those stakeholders can include members of management, security analysts, network engineers, application owners, and even your external partners (MSPs, VoIP, ISPs, etc.). This data, combined with application and user awareness information, will offer a detailed view of your environment.

Akins IT
NOVEMBER 22, 2019
The benefit now is that these policies can be built out and managed using a familiar NGFW GUI, and traffic can be inspected using UTM (Unified Threat Management) features such as Antivirus (AV), Intrusion Prevention System (IPS), Web and Application content filtering. INTERESTED IN VIEWING THE WEBINAR VIDEO ON THIS TOPIC?

CATO Networks
SEPTEMBER 27, 2017
Networking teams focussed on the connectivity between locations; security teams focussed on protecting against malware threats and other external or application-layer security issues. Any SD-WAN should build a virtual overlay of encrypted tunnels between locations.

CATO Networks
FEBRUARY 16, 2023
Double Extortion: Double extortion ransomware both steals and encrypts sensitive and valuable data on an infected system. Lateral Movement: Ransomware rarely immediately lands on a device containing the high-value data that it plans to encrypt. This model increased the number of companies infected with high-quality ransomware.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content