Where Do I Plug It? the dissolving perimeter and the insertion dillema
CATO Networks
JULY 29, 2015
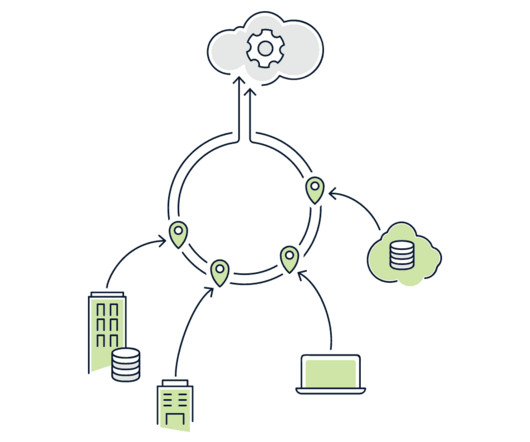
This was the way firewalls, intrusion prevention systems, email security gateways, data loss prevention and other security systems were implemented. There are two big forces that are pressuring this approach to network security: the use of public Cloud applications and the mobile workforce.





















Let's personalize your content