The role of email security in reducing user risk amid rising threats
CloudFaire
DECEMBER 19, 2024
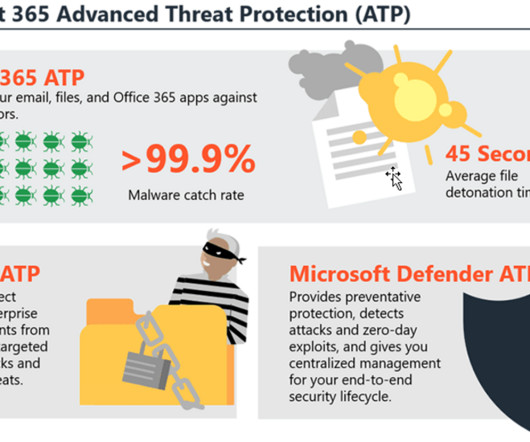
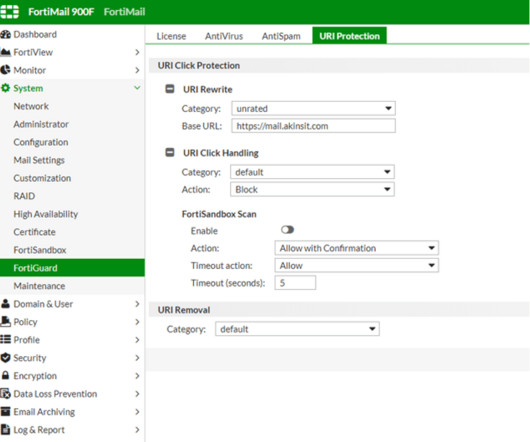
Modern attacks use a growing arsenal of deceptive techniques that bypass traditional secure email gateways (SEGs) and email authentication measures, targeting organizations, employees, and vendors. Phishing is no longer just an email problem its a multi-channel, cross-application threat.






































Let's personalize your content