Why is my SaaS application so slow?
Kentik
DECEMBER 13, 2021
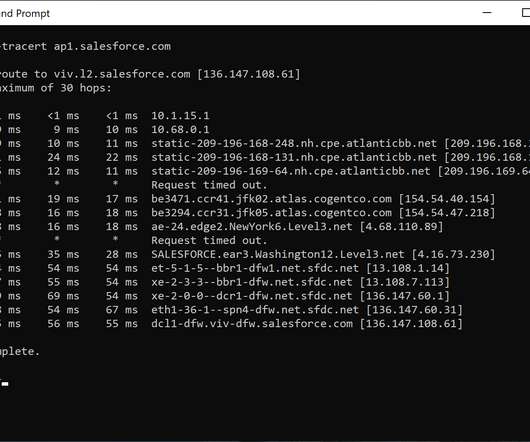
Some users simply can’t operate in their job when an application becomes unavailable. That’s why keeping a proverbial finger on the pulse of application performance is generally worth the effort. Many popular SaaS applications are delivered from hundreds of locations around the world. Check with the SaaS application.










Let's personalize your content