EP147: The Ultimate API Learning Roadmap
ByteByteGo
JANUARY 25, 2025
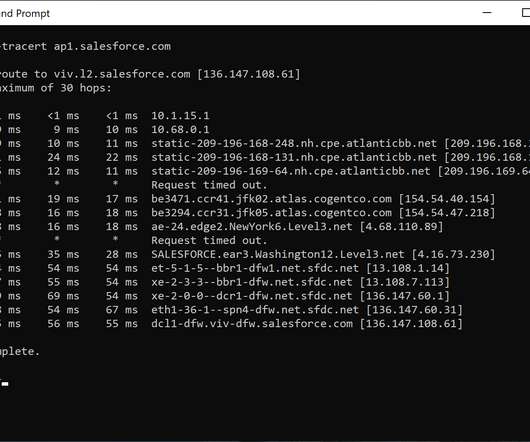
(Youtube video) The Ultimate API Learning Roadmap 30 Useful AI Apps That Can Help You in 2025 10 Essential Components of a Production Web Application How do we design effective and safe APIs? Explained With Simple Terms Session, Cookie, JWT, Token, SSO, and OAuth 2.0 After DNS resolution, the requests reach the app servers.










Let's personalize your content