Network Security and Direct Internet Access: The Foundation of MPLS WAN Transformation
CATO Networks
SEPTEMBER 15, 2018
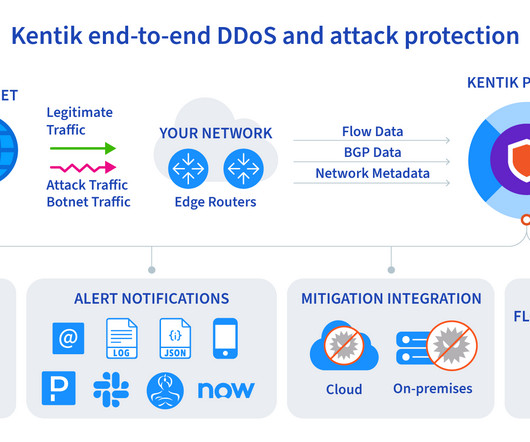
We were a bit surprised to find out that secure, direct Internet access was the top driver. We expected other drivers, such as MPLS cost reduction, eliminating bandwidth constraints, or optimizing cloud access, to be at the top of the list. Why is security such a big deal with SD-WAN?








































Let's personalize your content