Understanding Palo Alto Networks: A Comprehensive Guide
NW Kings
JANUARY 14, 2025
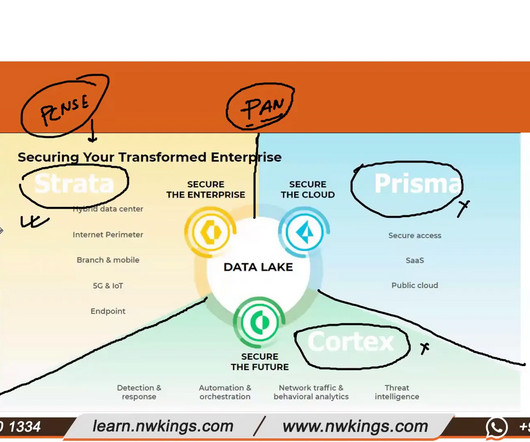
Prisma Prisma is a cloud security solution that is aimed at delivering security to cloud-based applications and data. Application Control: Manages and secures application usage across the network. The software is mainly for the protection of users and applications wherever they may be positioned.














Let's personalize your content