How WPA3 and Cisco Routers Enhance Your Network Security
Router-switch
OCTOBER 14, 2024
This article explains WPA3, its benefits, and the reasons that upgrading to a Cisco router that supports WPA3 might significantly increase network security.

Router-switch
OCTOBER 14, 2024
This article explains WPA3, its benefits, and the reasons that upgrading to a Cisco router that supports WPA3 might significantly increase network security.

CATO Networks
MARCH 8, 2017
Security – What do you need to secure the Internet access points at each of your offices? With security, for example, do you want to offload Internet traffic at the branch or backhaul traffic to the datacenter? But with Internet offload youll have another consideration — remote office network security.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
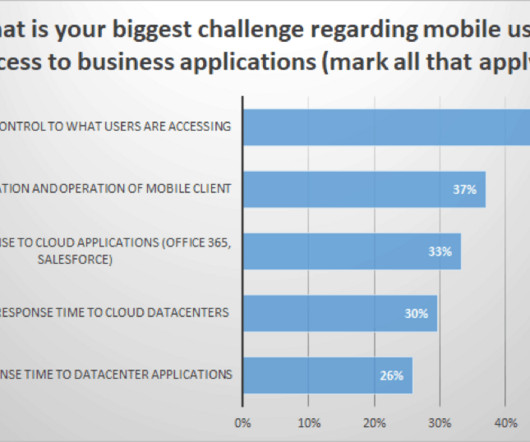
CATO Networks
NOVEMBER 27, 2017
From there, they can exit through a local Internet access point or traverse the WAN to a central, secured Internet access point. Either approach impacts performance, rendering traditional VPN architectures a poor choice for accessing cloud datacenters and applications.

CATO Networks
SEPTEMBER 27, 2017
The market for SD-WAN has been driven in part by its ability to reduce bandwidth costs and improve the performance of cloud access. These drivers, though, also come with baggage: the reassessment of todays corporate security model. Traditionally, Wide Area Networks (WANs) and network security were loosely coupled entities.

Kentik
NOVEMBER 7, 2018
Azure flow logging is a feature of Azure Network Watcher, a tool used to monitor, diagnose, and gain insights into Azure cloud’s network performance and health. Azure flow logging allows you to view information about ingress and egress IP traffic through a Network Security Group (NSG). Virtual network TAP.

CATO Networks
NOVEMBER 19, 2019
The traffic is then routed on to a local Internet access point or across the WAN to a centralized and secure Internet access point before making its way to its destination in the cloud. This approach creates significant impact on performance, making it unattractive to most enterprises.

CATO Networks
SEPTEMBER 5, 2018
No Security – SD-WAN appliance solutions dont provide any security, so security must be added to the solution via service-insertion or service-chaining. How will they secure all of the Internet access points created by SD-WAN?
Let's personalize your content