KRACK Kills
Akins IT
OCTOBER 17, 2017
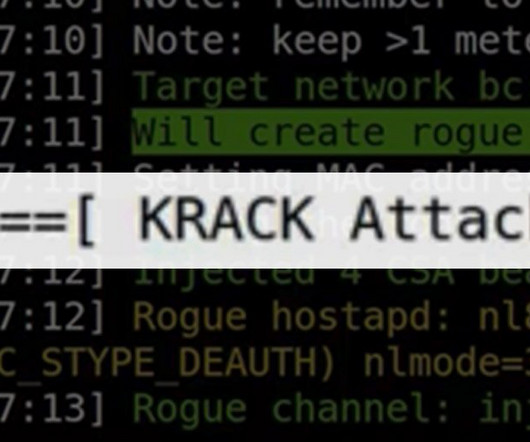
Its important to understand how this large scale wireless encryption exploit operates and how you can take preventative measures to protect your network from the KRACK exploit and future security compromises to come. WPA and WPA2, an otherwise ubiquitous wireless encryption standard was at the center of the exploit. What Can I Do?













Let's personalize your content