Why Traditional MPLS Networks are Ill-Suited for UCaaS
CATO Networks
NOVEMBER 26, 2018
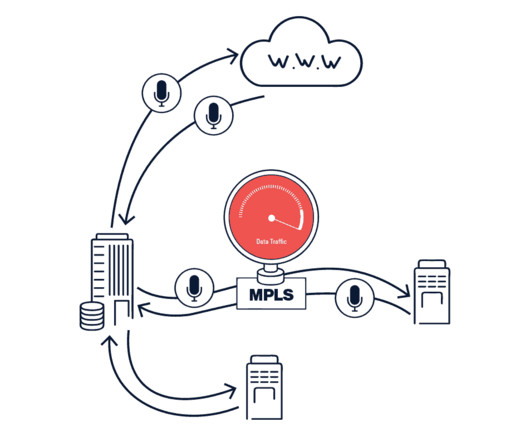
Most enterprise data networks are still optimized for a computing model in which the bulk of applications reside in the datacenter. Thus, all access to Internet-based apps requires routing flows from the branch to the headquarters or datacenter location, and then out to the Internet. The answer?











Let's personalize your content